
Traditional security approaches aren’t closing the gap fast enough against the onslaught of cyberattacks growing in severity and sophistication every day. Attackers sharpening their tradecraft and looking for the weakest areas of businesses to attack made 2023 the year that will be remembered for a drastic rise in cyber threats.
Cloud intrusions jumped 75%, there was a 76% increase in data theft victims named on data leak sites and a 60% increase in interactive intrusion campaigns. Worse, 75% of attacks were malware-free, making them difficult to identify and stop. There was also a 110% YoY increase in cloud-conscious cases – with Scattered Spider predominantly driving activity.
Further underscoring just how wide the gap is between where attackers are from an efficiency standpoint and how effective legacy security approaches are, attackers trimmed 17 minutes off their average eCrime intrusion activity time results. In 2023, the average breakout time for eCrime intrusion activity decreased from 79 minutes in 2022 to 62 minutes in 2023, leaving defenders only an hour’s worth of time to minimize the cost and damage caused by the intrusion. The fastest observed breakout time was only 2 minutes and 7 seconds.
CrowdStrike’s 2024 Global Threat Report published today shows how attackers’ tradecraft is progressing significantly faster than existing and legacy cybersecurity solutions can keep up. Combining generative AI, special engineering, interactive intrusion campaigns, and an all-out assault on cloud vulnerabilities and identities, attackers are executing a playbook that seeks to capitalize on the weaknesses of organizations with outdated or no cybersecurity arsenals in place.
VB Event
The AI Impact Tour – NYC
We’ll be in New York on February 29 in partnership with Microsoft to discuss how to balance risks and rewards of AI applications. Request an invite to the exclusive event below.
CrowdStrike discovered 34 newly named attackers last year, including Egypt-based adversary Watchful Spinx, and is now tracking more than 232 globally. There are 130 active malicious activity clusters also being tracked in real time.
Criminal and nation-state adversaries are growing at a double-digit annual growth rate, with the nation-state and activist attackers being among the most prolific. Source: CrowdStrike
CrowdStrike’s report provides a glimpse into how quickly the global threat landscape is changing. Of the many threats they’ve analyzed and provided evidence on, five cyber threats are the most alarming.
The five cyber threats described below reflect how attackers are getting more efficient at exploiting identities, cloud infrastructures and third-party relationships. The following is an overview of the most critical cyber threats identified in the report to help organizations be more knowledgeable about them to strengthen their defenses further.
- Identity-based and social engineering attacks are reaching a new level of intensity. Relying on advanced phishing to mimic legitimate users and infiltrate secure accounts, attackers are showing a new level of intensity in their identity-based and social engineering attacks. Attackers have long sought account credentials, but in 2023, their goals centered on authentication tools and systems, including API keys and OTPs.
“What we’re seeing is that the threat actors have really been focused on identity, taking a legitimate identity. Logging in as a legitimate user. And then laying low, staying under the radar by living off the land by using legitimate tools,” Adam Meyers, senior vice president counter adversary operations at CrowdStrike, told VentureBeat during a recent briefing.
Two of the most infamous Russian nation-state attackers, Fancy Bear and Cozy Bear led these efforts, with the form exploiting a Microsoft Outlook vulnerability (CVE-2023-23397) for unauthorized server access. Scattered Spiner, part of an eCrime syndicate, relies on tactics including smishing and vishing. Their attacks are known for exhibiting a nuanced understanding of security policies to breach accounts. The graphic below is the anatomy of an identity-based attack.
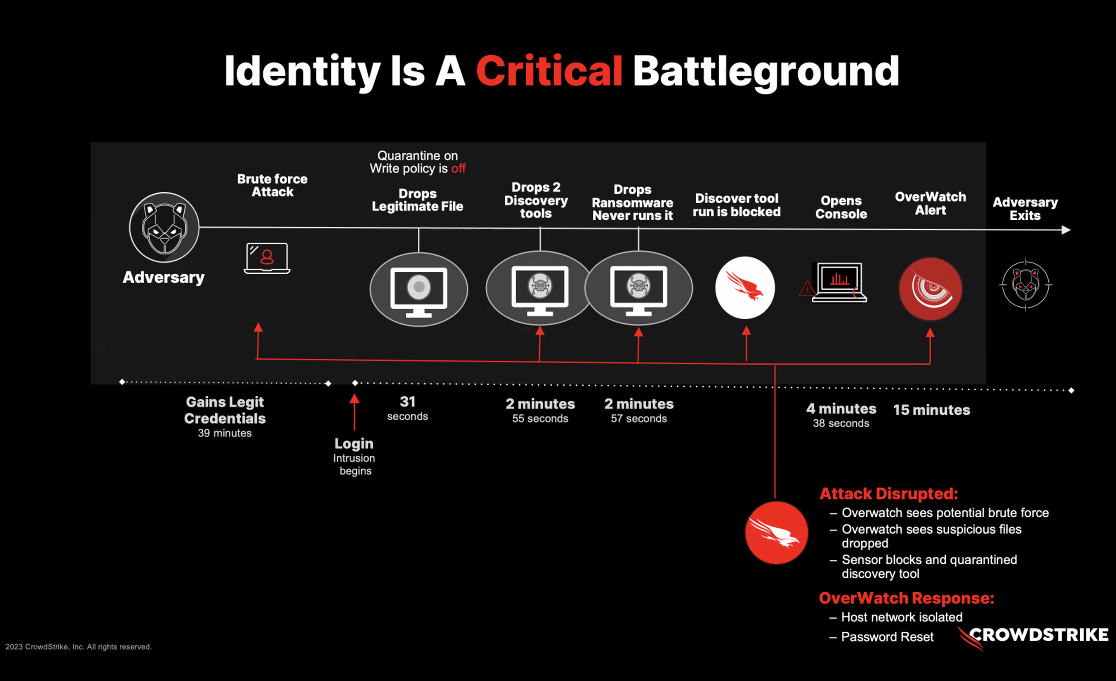
The anatomy of an identity attack. Note the elapsed time along the center dotted line. Stopping a breach is getting harder to do as attackers find new ways to gain speed advantages. Source: Crowdstrike
- Cloud intrusions soared last year, growing 75% year-over-year. Cloud misconfigurations are common, and they’re the weakness attackers look for first when they’ve chosen an organization to attack. CrowdStrike’s analysis found that attackers are getting more savvy in how they attack cloud threat surfaces. There was a 110% rise in cloud-conscious cases—where attackers exploit cloud-specific features—and a 60% increase in cloud-agnostic incidents. ECrime attackers are responsible for 84% of these breaches, and they’re showing a strong preference for identity-based attack techniques, targeting everything from credentials to API keys. CrowdStrike found that Scattered Spider accounts for 29% of attack incidents by using advanced methods to infiltrate cloud environments. Closing the gaps in multicloud configurations is a given. The current and future generations of AI-based cloud configuration tools and apps are critical for organizations to scan and protect their cloud infrastructure regularly.
- Attackers known for Big Game Hunting (BGH) expertise in 2023 are pivoting to data theft and extortion over ransomware. CrowdStrike found that cybercriminal-based Graceful Spyder is shifting tactics, focusing on data theft and extortion over ransomware. The attacker is known for its expertise in exploiting zero-day vulnerabilities and has targeted more than 380 known organizations. They’re also known for publishing stolen data on Dark Leak Sites and clearweb domains. Known for publishing sensitive records and admin credentials to coerce victim payments, Graceful Spynder and comparable attackers have also started to report victims who are publicly traded to the U.S. Securities And Exchange Commission to force payments.
- Third-party relationship exploitation is increasing, with nation-state attackers leading the way. Nation-states increased their attack strategies aimed at exploiting third-party relationships to breach networks with a strong focus on the technology sector via vendor-client connections. Attacks share a common series of traits, including relying on software supply chain and IT service compromises for initial access. CrowdStrike found China-nexus groups, including Jackpoint Panda and Cascade Panda, were the most active. DPRK’s Labrinth Chollima was tracked deploying malware, including XShade and WinDealer, for surveillance, espionage, and crypto theft, a common strategy they use to finance their missile and weapons programs. These attacks are a grim reminder that every software supply chain is at risk. Improving vendor risk management to prevent widespread downstream compromises is a given.
- Nation-state attackers are accelerating on the gen AI learning curve and it’s going to increase in 2024. The first gen AI-based attack tools, including FraudGPT, quickly launched after OpenAI’s launch of ChatGPT in late 2022. Since then, CrowdStrike’s Counter Advisory Operations (COA) have seen attackers continually improving their tradecraft. Scattered Spider used generative AI to launch attacks against North American financial entities. COA also discovered a Chinese campaign that successfully used gen AI to divert social media influence. More cybersecurity companies need to fast-track their use of defensive AI to give businesses a fighting chance of winning the AI war.
Every business needs to get prepared
CrowdStrikes’ latest report highlights how essential identity protection, ongoing cloud configuration management and securit, and continued investments in cross-domain visibility are. The one area where nation-state attackers have a strong advantage, however, is speed.
VentureBeat often hears from CISOs how important consolidating their tech stacks is to improve visibility while reducing costs. Advances in AI-based extended detection and response (XDR), endpoint security management, and improved security posture management – all driven by real-time telemetry data interpreted and acted on – are essential.
The bottom line is that AI needs human insights to reach its full potential. AI shouldn’t be looked at as a replacement for security Operations center (SOC) analysts or experienced threat hunters. Rather, AI’s apps and platforms are tools threat hunters need to better protect enterprises. Human-in-the-middle designs of AI platforms are table stakes for improving the accuracy and speed of intrusion and breach response.
VentureBeat’s mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Discover our Briefings.





