
Are you ready to bring more awareness to your brand? Consider becoming a sponsor for The AI Impact Tour. Learn more about the opportunities here.
AWS‘s vision for achieving stronger, more resilient cloud security relies on implementing generative AI, human insight, and improved usability correctly with every product release — all from a posture of zero trust.
Steve Schmidt, Chief Security Officer at Amazon, made this point clear during his keynote speech today at the cloud leader’s annual large conference, re:Invent 2023.
Titled Move fast, stay secure: strategies for the future of security, Schmidt’s speech emphasized that cloud security needs to be prioritized as a business enabler first if it is going to succeed.
As such Schmidt also introduced a range of new AWS cloud security updates and products, including Amazon Detective and Amazon GuardDuty.
VB Event
The AI Impact Tour
Connect with the enterprise AI community at VentureBeat’s AI Impact Tour coming to a city near you!
Playing detective and standing guard
Amazon Detective reflects AWS’s focus on providing insights into cloud security events and investigations, supporting Identity Access Management (IAM), finding group summaries with generative AI, initiating security investigations with GuardDuty ECS Runtime Monitoring, and integrating with Amazon Security Lake.
Amazon GuardDuty is designed to detect runtime security teams in Amazon Elastic Container Services clusters (ECS) running on AWS Fargate and Amazon Elastic Compute Cloud (Amazon EC2).
Additional services mentioned during the keynote include Amazon Code Whisperer, allowing AWS customers to connect with internal code stores and create customizations. Also mentioned were Amazon Bedrock and AWS IAM (Identity and Access Management) Access Analyzer. AWS’ security attendee’s guide to AWS re:Invent 2023 provides a complete list of all breakout sessions, chalk talks, workshops and builder sessions.
Virtual private clouds (VPCs) for security
AWS emphasized that securing customers’ virtual private clouds (VPC) continues to be a catalyst they rely on for continually improving their customers’ network security. Schmidt alluded to the releases of the VPC reachability analyzer and the network access analyzer. These two services, Schmidt says, can prove whether VPC or network resources are reachable from the Internet. The graphic below shows how AWS positions these solutions in the context of VPCs.
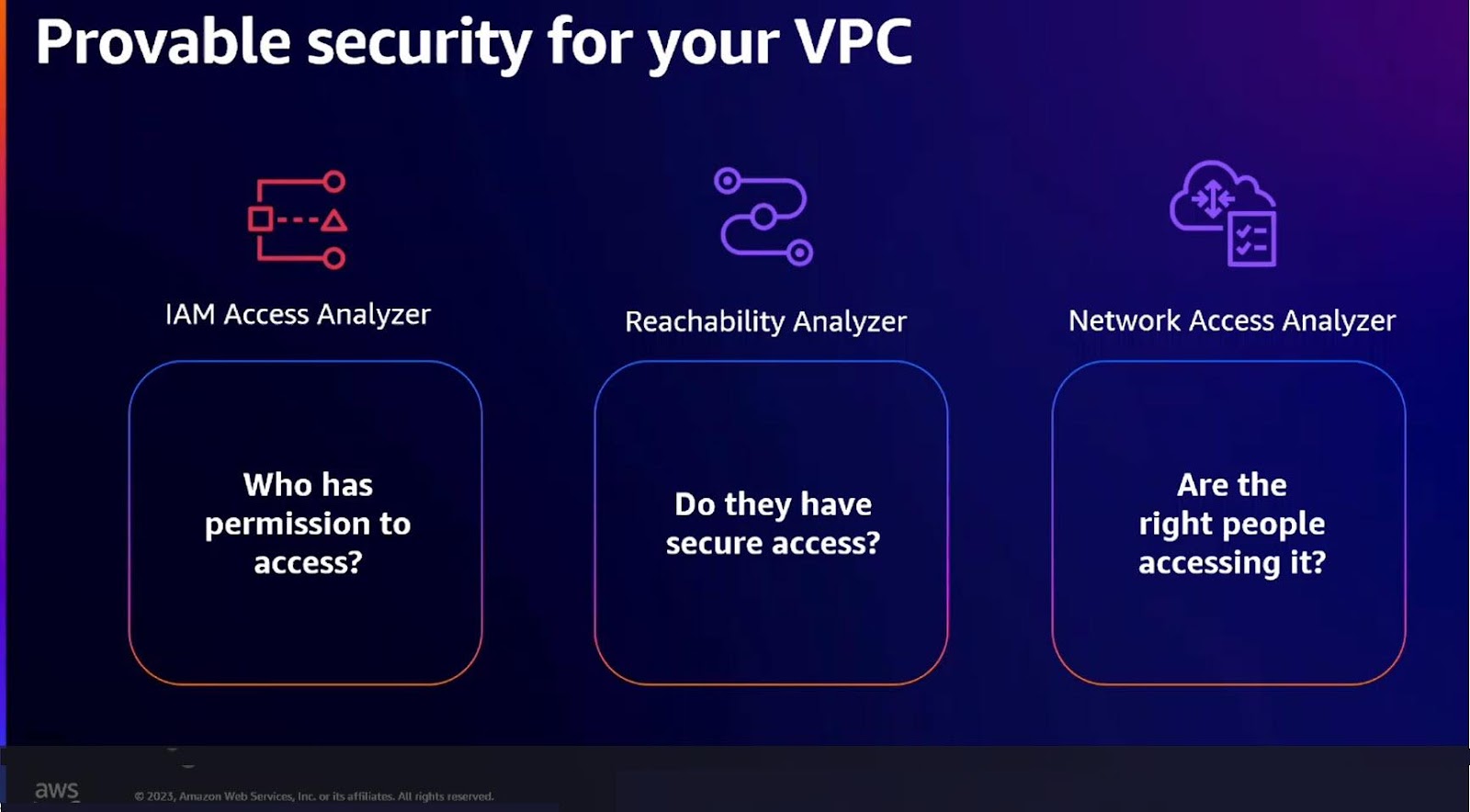
CAPTION: Securing AWS’ customers’ Virtual Private Clouds (VPC) is a driving force for innovation, as reflected in the latest updates mentioned during Schmidt’s keynote. Source: Innovation Talk, Move fast, stay secure: Strategies for the future of security
Balancing gen AI with human expertise
Schmidt explained that the AWS cloud security vision looks to capitalize on the rapid advances gen AI, AI, and machine learning (ML) models deliver to strengthen human insights and contextual intelligence. AWS sees gen AI and its related technologies as symbiotic and strengthening human insight and intelligence, providing security teams with new knowledge not available given existing tools’ limitations.
“Generative AI is one more tool our teams are using to help our customers be more effective in their work while raising a security bar,” Schmidt said.
“AI delivers the best results when it makes expert knowledge available in a context where you can act on that knowledge. At Amazon, we’ve seen this pattern reward repeatedly when it comes to security. AI is making security knowledge and deep subject matter expertise widely available,” Schmidt continued.
AWS’s commitment to customers is that it will continue capitalizing on rapid advances in AI and ML, nuanced with human expertise to identify threats with greater accuracy.
Schmidt also explained how AWS uses large language models (LLMs) internally to speed up the application security review process. The LLMs provide support and data for engineers who adapt their findings with human insight.
All-in on zero trust
Schmidt said he often discusses authentication and authorization with CISOs at AWS customers. Those conversations tend to turn toward zero trust, the security practice that assumes all users and third-parties who interact with a system could be potential threats. Schmidt says it’s time to get on the same page when discussing zero trust.
“What I hear from other CISOs is that they need to make decisions around authentication and authorization with more granularity, flexibility, and frequency. Days of relying on overly simplified models where everything outside is bad and everything inside is good are long gone. Those simplified approaches slow down business innovation and leave too many gaps in our security posture,” he observed.
Schmidt is referring to cybersecurity platforms and systems that assume any identity, device, or endpoint is safe once up and running inside a firewall. At its core, the zero trust framework is about granting least privilege access and monitoring every interaction on a network.
Schmidt elaborated on AWS’ being all in on zero trust, observing, “zero trust is built on the foundation of authentication and authorization. So, for our discussion on zero trust, let’s work with just one simple goal. Let’s talk about how to more precisely and scalably control authentication.”
“At AWS, we see zero trust as a model where security controls are applied to your assets. Assets don’t rely solely on traditional network parameters. The model uses identity device attributes and other signals to help you make continuous adaptive and nuanced access control,” Schmidt observed.
VentureBeat’s mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Discover our Briefings.





